Reverse Engineering
Static analysis
How to know if a binary is packed
- PEid
- Raw Size and Virtual Size are very different
- Character strings are random.
- Non-standard section names (UPX0, ...)
- Dependency viewer
- Low number of imports
Extract resource section from a binary
- Resource Hacker
- if a binary contains resources (section .rsrc), it's possible to view/extract it with this software).
UPX
UPX, is a tool called packer, used to pack/unpack a binary.
Dynamic analysis
- procmon - monitor the actions performed on the system when malware is launched
- process explorer - obtain information on the process in memory (there may be differences between the binary on disk and what runs in memory - (strings present, DLLs loaded, etc.))
- inetsim - simulate network responses to allow malware to continue executing normally (if in multiple VMs, change
DNS IPandbind_addressto listen on all interfaces, not just local) - wireshark - capture network traffic
- regshot - capture windows registry before and after malware execution
If you need to analyze a DLL, you can execute with cmd.exe using the following command:
rundll32.exe <dll_path>, <exported_func>
A few tips on using IDA
-
to identify a local variable for a function, IDA specifies negative addresses (relative to esp) - otherwise it's an argument.

Some shortcuts
-
Rename what you understand, variables, functions... (keyboard shortcut:
n) -
Add comments (keyboard shortcut:
:) -
jump to a specific line (keyboard shortcut:
g) -
display cross-references (X-ref) (keyboard shortcut:
x)
How to read
mov dest, src
xor edx, edx ; sets edx to 0
Arguments are pushed on the stack, from right to left.
From the windows documentation socket windows documentation
SOCKET WSAAPI socket(
[in] int af,
[in] int type,
[in] int protocol
);

In this socket call, protocol=6, type=1 and af=2.
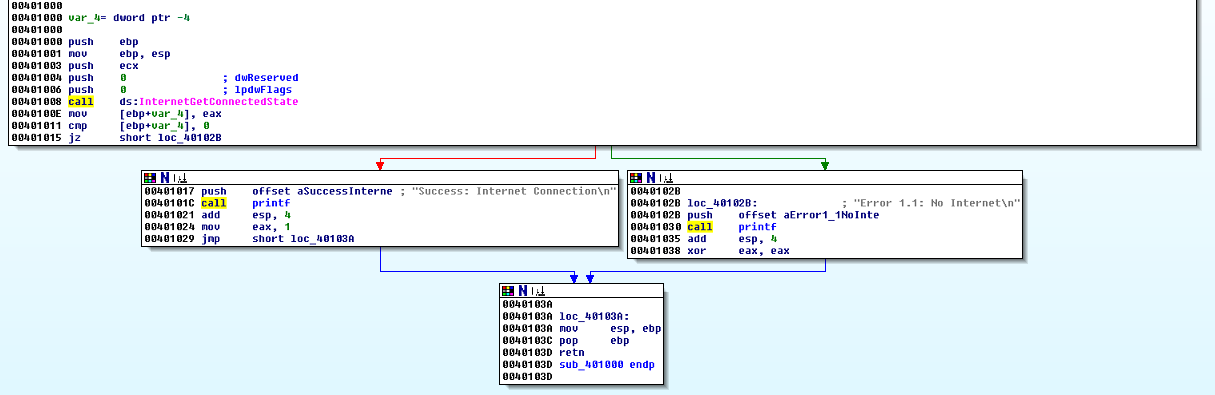
Quick binary analysis
In the functions tab, we search for the _main function, which is the entry point for our program.
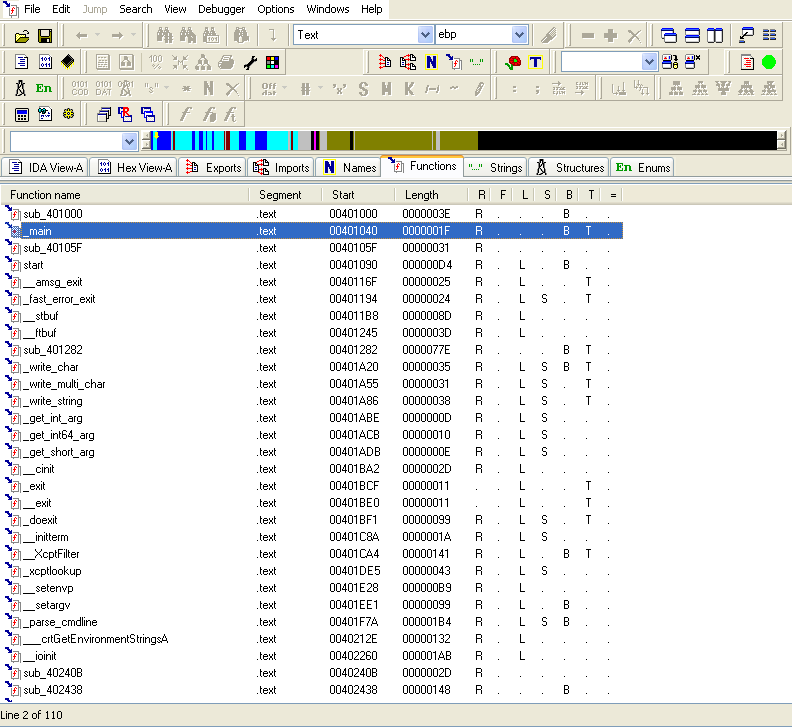
We finally realize that our binary contains a simple if displaying whether it has access to the Internet or not.
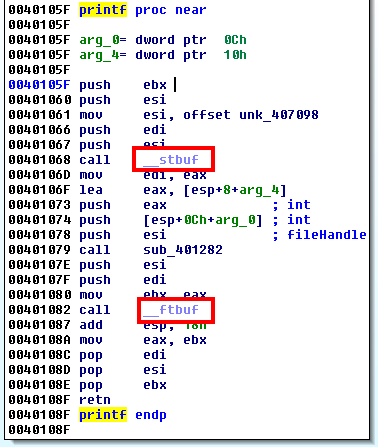
The
printffunction is not recognized by IDA, but you can tell it's this function by a quick scan. A call to_stbufand_ftbufis made.
The InternetReadFile function takes a buffer and buffer size as parameters. Here, we push 512 bytes (200h). Except that at declaration time, we notice that the Buffer variable (IDA didn't notice it was an array, so it just says it's a pointer) isn't 512 bytes (difference between Buffer and var_20c).
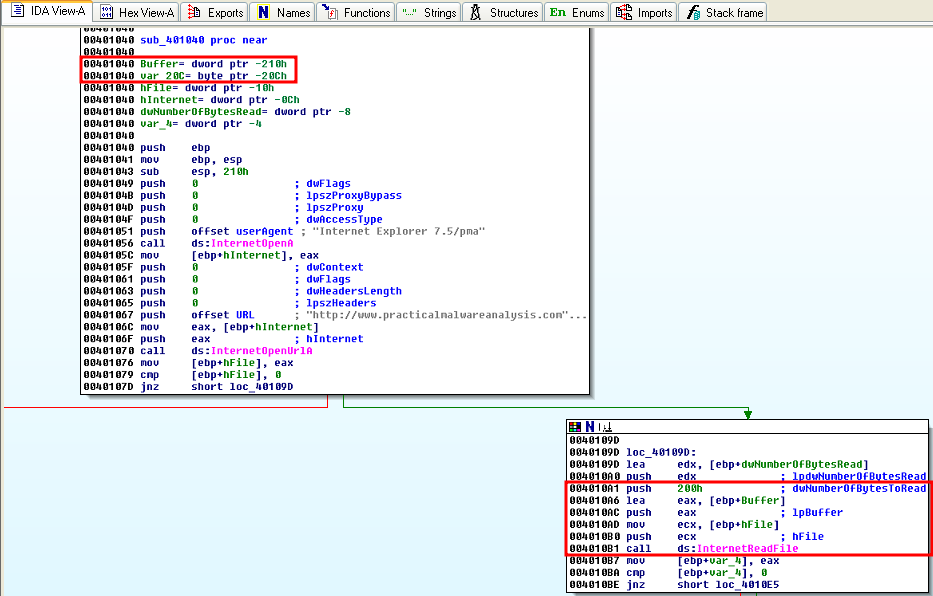
To modify this interpretation of IDA, move to the Buffer declaration, then ctrl+k.
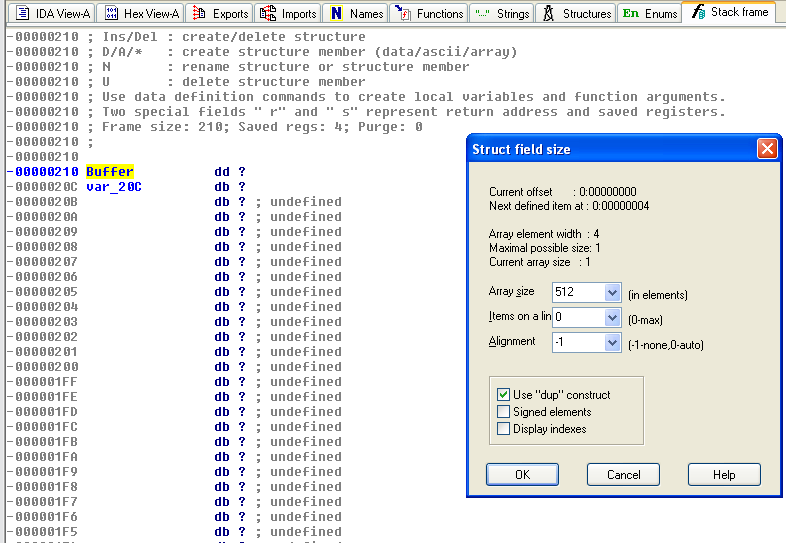
After modification:
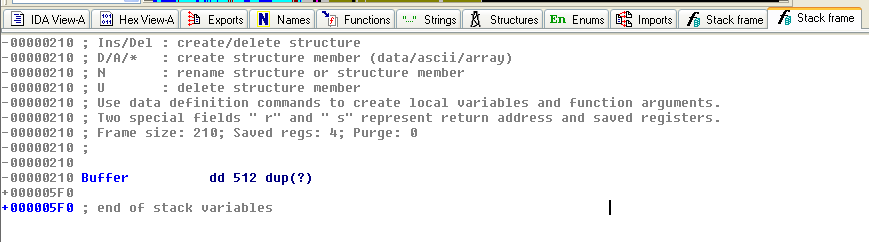
After the InternetReadFile function, the program checks the beginning of the response and look for a specific command so that it knows what to do next.
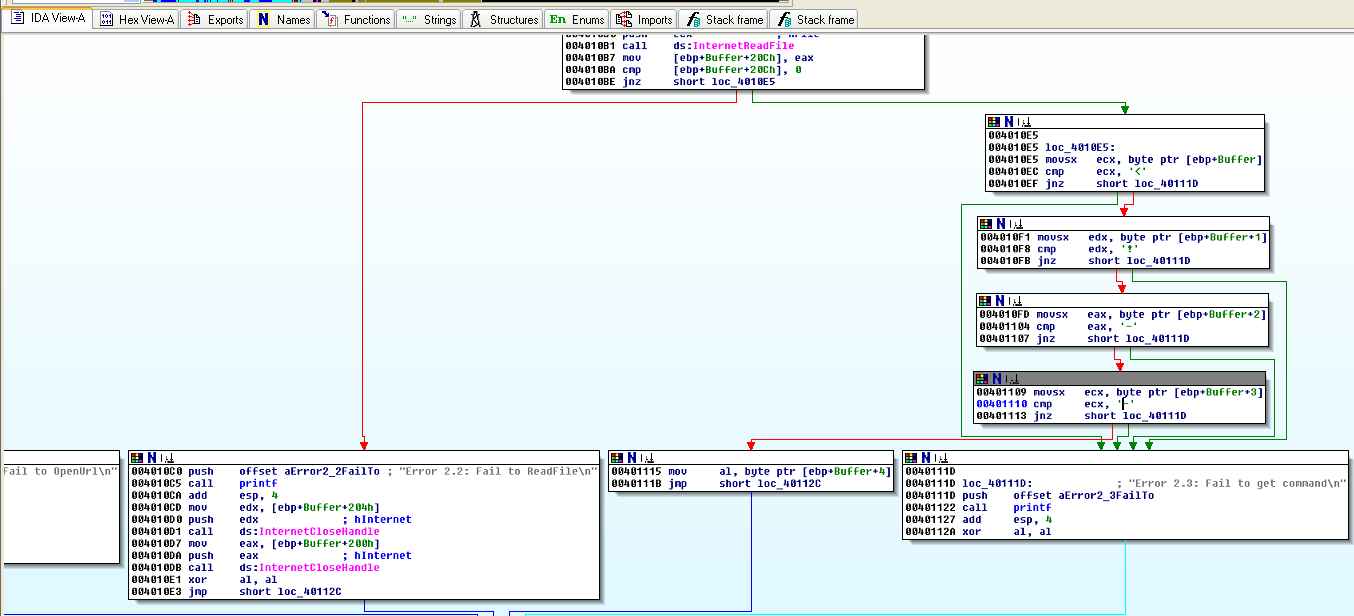
Valid commands are [a, b, c, d, e]
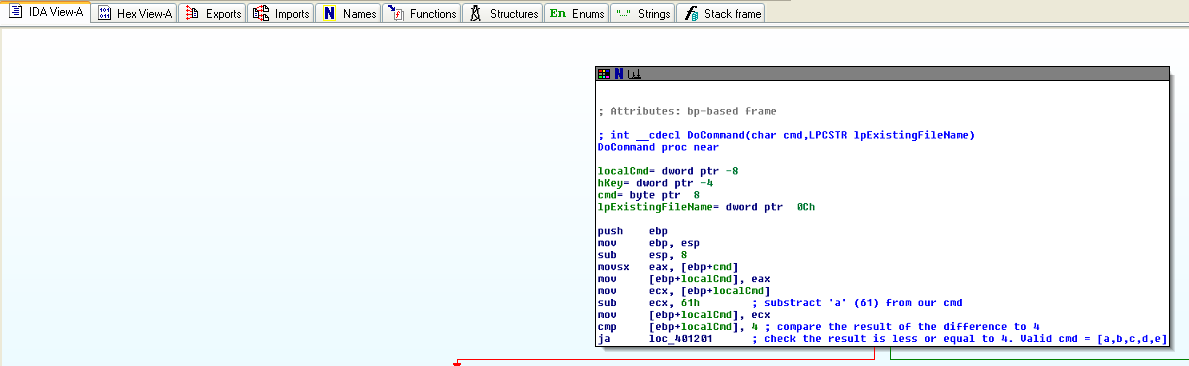
Dynamically testing commands
Appending a comment in the inetsim fake html page. (The a command should create a directory)
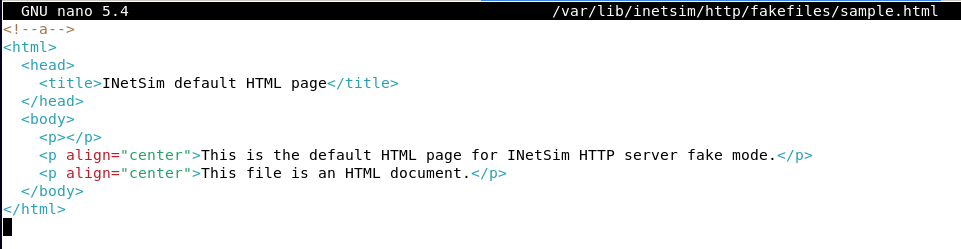
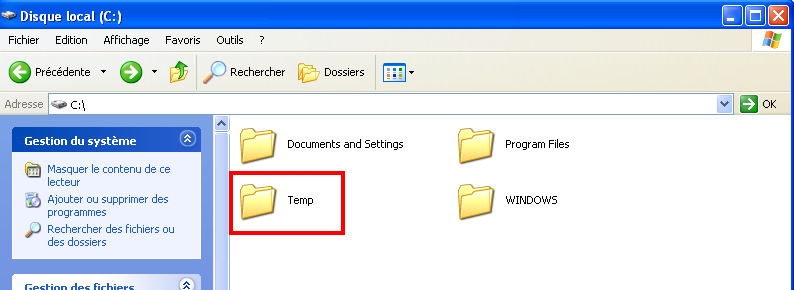
Executing the malware

The new Temp directory is then created
Hack weak strcmp code
A description of a basic hack over a C files using strcmp function. We will explain how to hack the executable a.out. When we execute we see that we are asked to enter a password:
$ ./a.out
the-password-you're-trying
You failed to log in. Try again :-(
Using gdb
We launch the debbugger on the binary:
gdb -q a.out
# We launch the program with a breakpoint on the main function:
(gdb) break main
# Breakpoint 1 at 0x40064a
(gdb) run
# Starting program: /path/to/file/a.out
# Breakpoint 1, 0x000000000040064a in main ()
(gdb)
# We can thus disassemble the code:
(gdb) disas main
# Dump of assembler code for function main:
# ...
# 0x0000000000400688 <+66>: mov %rax,%rsi
# 0x000000000040068b <+69>: mov $0x400776,%edi
# 0x0000000000400690 <+74>: callq 0x400520 <strcmp@plt>
# 0x0000000000400695 <+79>: test %eax,%eax
# 0x0000000000400697 <+81>: jne 0x4006a5 <main+95>
# 0x0000000000400699 <+83>: mov $0x400780,%edi
# 0x000000000040069e <+88>: callq 0x4004f0 <puts@plt>
# 0x00000000004006a3 <+93>: jmp 0x4006af <main+105>
# 0x00000000004006a5 <+95>: mov $0x4007a0,%edi
# ...
# End of assembler dump.
Modify it
The aim is to change the jne code (0x75) to the je code (0x74) in order to override the conditionnal stop after the strcmp.
We see at 0x0000000000400690 strcmp, this is a string comparison function, then a test and a conditional jump (jne). We can try to transform the jne (jump if not equal) into je (jump if equal) and then continue the program. The code of jne is 0x75, and that of je is 0x74:
(gdb) set {char}0x0000000000400697=0x74
(gdb) continue
# Continuing.
# Please enter the password:
# wecantapeanythingevenwrongpwd
# Congratulations you are log in
[Inferior 1 (process 3577) exited normally]
To note that another technique is to observe which strings are comparated by strcmp by putting breakpoint and manipulating register. Here we just bybass the comparaison mechanism
Using ltrace
ltrace is a debugging utility in Linux, used to display the calls a userspace application makes to shared libraries.
ltrace ./a.out
__libc_start_main(0x400646, 1, 0x7ffdb5632e68, 0x4006d0 <unfinished ...>
puts("Please enter the password:"Please enter the password:) = 27
__isoc99_scanf(0x400773, 0x7ffdb5632d60, 0x7fc613a0b780, 0x7fc61373c6e0, test) = 1
strcmp("hackm3", "test") = -12
puts("You failed to log in. Try again "...You failed to log in. Try again :-() = 36
We see that the strcmp("hackm3", "test") is exposed in clear and so we can retrieve the password.